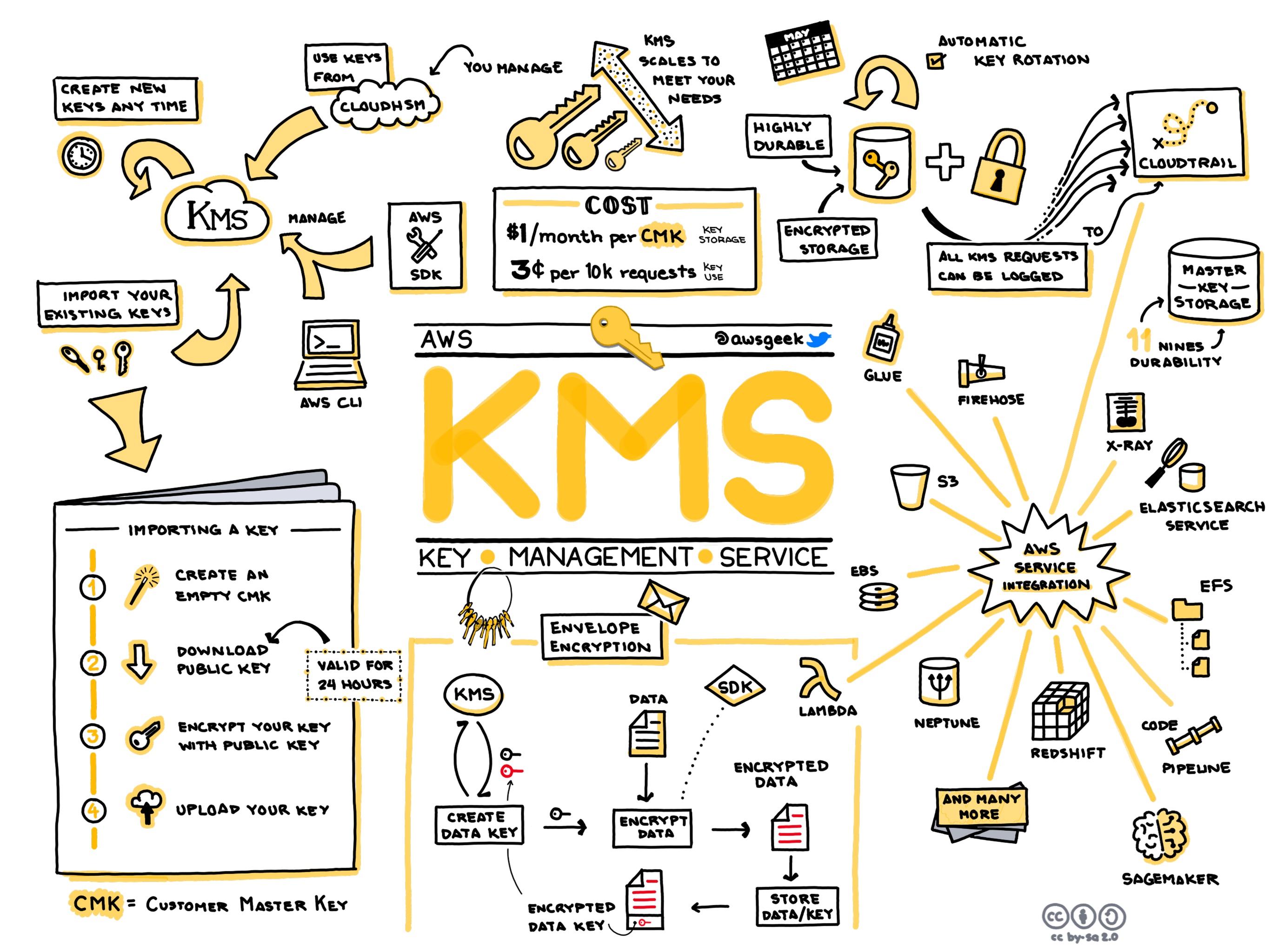
AWS Key Management Service (KMS) is a critical part of AWS's security infrastructure, allowing developers and IT administrators to create, manage, and control cryptographic keys across their AWS cloud infrastructure and applications. KMS is designed for a wide range of use cases, providing scalability and availability while maintaining stringent security measures. Understanding the technical aspects of AWS KMS can empower teams to leverage encryption effectively in their cloud architecture, ensuring data protection and compliance with industry standards.
Use Cases
AWS KMS is employed in various scenarios, such as securing data at rest and in transit. It is integral to encrypting S3 buckets, safeguarding data stored in RDS, and ensuring secure communications with Amazon EBS. Developers can use AWS KMS to easily integrate encryption into their applications using SDKs and APIs, supporting multi-region and hybrid environments. IT administrators often use AWS KMS for managing keys in Identity and Access Management (IAM) to restrict access and ensure only authorized users can decrypt sensitive data. Migrating workloads to AWS with encryption can meet compliance demands for industries such as healthcare and finance, where data privacy is paramount.
Pricing
The AWS KMS pricing model is based on two primary factors: key usage and requests to the service. The costs are segmented into symmetric and asymmetric key charges. Symmetric keys incur lower charges, while asymmetric keys, being computationally intensive, are more expensive to operate. Request costs are also involved, which include API calls for encryption, decryption, and key management operations. AWS offers detailed pricing, allowing users to estimate costs based on projected use, ensuring that KMS remains a cost-effective solution in both small-scale and enterprise environments.
Scalability
AWS KMS is designed to scale with the demands of an organization. The service handles millions of requests per second and supports automatic scaling based on the workload requirements. Users can leverage the KMS multi-Region keys feature, which allows them to replicate cryptographic keys across different AWS regions. This capability aids in global application deployments, ensuring encrypted data is accessible and compliant with local data residency requirements. The seamless integration with other AWS services enhances its scalability, making KMS a pivotal service for organizations with rapidly growing data encryption needs.
Availability
AWS KMS boasts high availability through its multi-AZ architecture, ensuring that cryptographic operations are resilient to failures within a singular availability zone. Key redundancy is inherent within the service, offering fast failover and recovery options. The integration with AWS CloudTrail ensures comprehensive logging and monitoring of all key management activities, offering administrators insights into key usage patterns and security anomalies. With an SLA that guarantees 99.9% availability, AWS KMS is a reliable choice for mission-critical applications requiring continuous uptime.
Security
Security is foundational to AWS KMS, encapsulating enterprise-grade encryption capabilities. Keys are secured through the use of Hardware Security Modules (HSM) during their creation, adding a layer of physical security to the software offerings. The service supports key rotation, automated through both user-defined policies and AWS's managed rotation, ensuring compliance with security protocols. AWS KMS provides granular access control integrated with IAM, allowing for fine-grained permissions over who can manage keys and perform cryptographic operations. The service also supports AWS Audit Manager for continuous compliance and assessment against regulatory frameworks.
Competition
In the cloud services industry, several competitors offer similar key management solutions. Alibaba Cloud offers Key Management Service for cryptographic needs, featuring robust integration with their cloud products. For more information, visit Alibaba Cloud KMS.
Google Cloud provides Cloud Key Management, enabling encryption for GCP resources and offering API-driven key management. Detailed information can be found at Google Cloud KMS.
Microsoft Azure includes Azure Key Vault, designed for storing secrets, keys, and certificates, with comprehensive monitoring and access control. For more details, see Azure Key Vault.
These services are tailored to work seamlessly within their respective cloud ecosystems, providing options for users who require secure and efficient key management infrastructure.
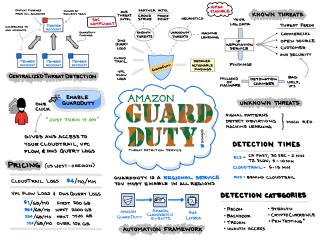 Amazon GuardDuty
Amazon GuardDuty
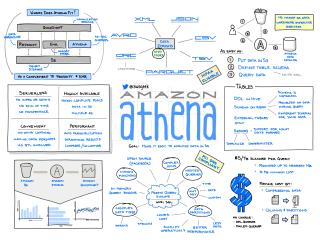 Amazon Athena
Amazon Athena
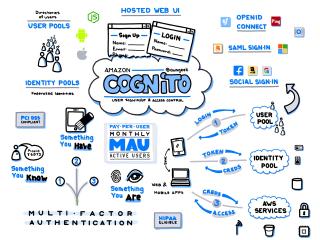 Amazon Cognito
Amazon Cognito
 Amazon Macie
Amazon Macie