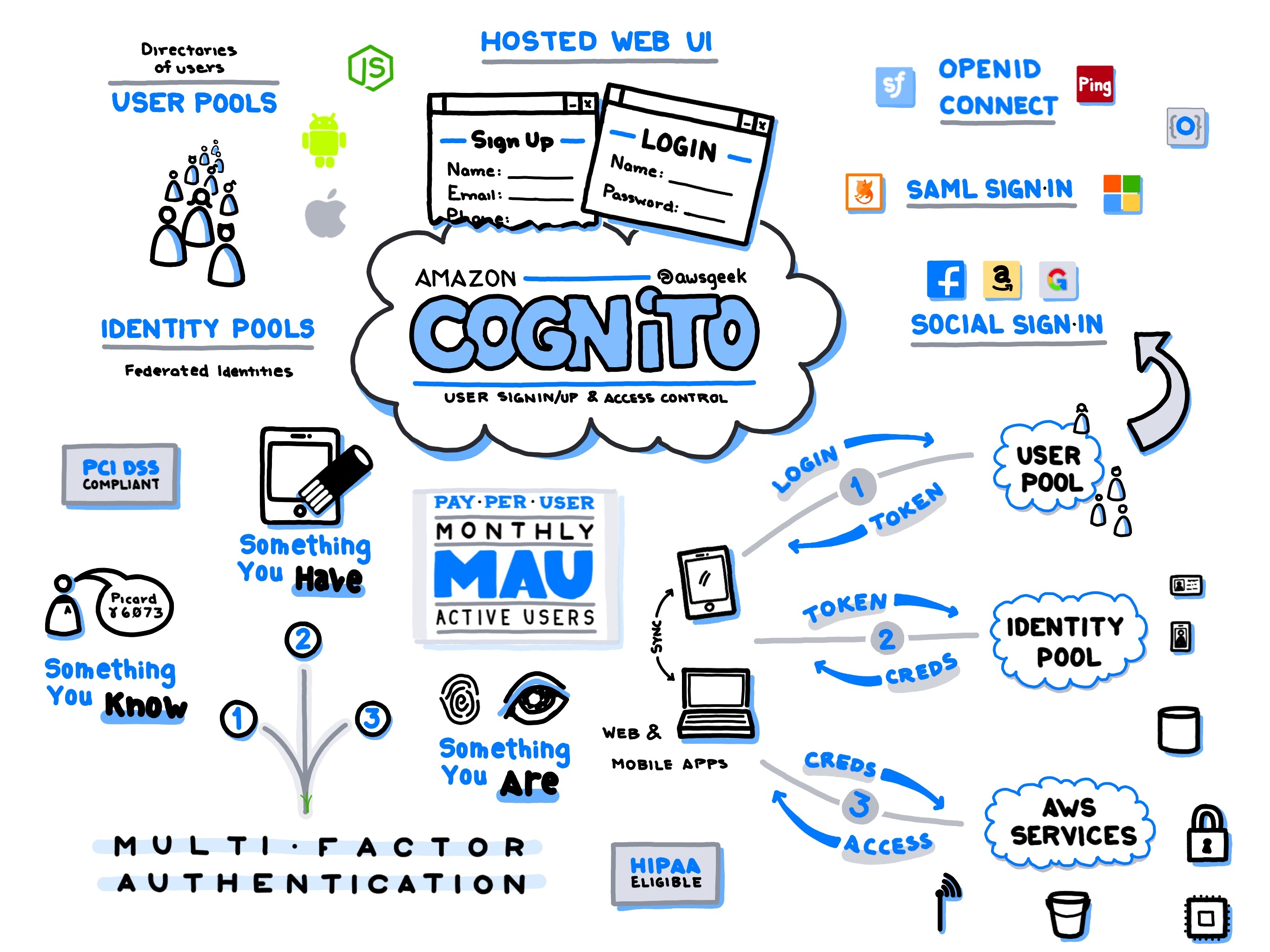
Amazon Cognito is a user identity and data synchronization service that helps manage authentication, authorization, and user management for web and mobile apps. It offers a robust feature set designed to streamline the development of secure applications by handling user authentication, account verification, and user pool management at scale. Ideal for developers seeking to incorporate secure user authentication mechanisms without delving deeply into the complexities of security protocols, Amazon Cognito integrates seamlessly with AWS services such as AWS Lambda, Amazon API Gateway, and Amazon S3.
Use Cases
Amazon Cognito is widely used in scenarios requiring secure and scalable user identification and management. It is a popular choice for apps demanding robust user pool management capabilities, such as e-commerce, social networks, and enterprise software, where user data synchronization across devices is critical. Additionally, Amazon Cognito supports Social Identity Providers like Google, Facebook, and Amazon, simplifying the implementation of Single Sign-On (SSO) in consumer-facing applications. Its secure token service is particularly beneficial for securing APIs, providing temporary AWS credentials for app users.
Pricing
Amazon Cognito's pricing is based on two key factors: the number of monthly active users (MAUs) and the number of minutes used in real-time sync operations. The User Pools feature allows free usage of up to 50,000 MAUs per month. Beyond this threshold, a tiered pricing model applies, which becomes quite economical as usage scales. The Sync feature follows a similar model, with charges incurred based on data storage and the volume of data sync operations conducted.
Scalability
Designed inherently to handle heavy traffic, Amazon Cognito can effortlessly scale to accommodate millions of users. By leveraging Amazon's cloud infrastructure, it provides automatic scaling capabilities that adjust based on demand, without requiring manual intervention. This makes it suitable for both small-scale applications and large-scale enterprise environments where user bases can vary significantly and unpredictably.
Availability
Amazon Cognito services are deployed in multiple AWS Regions, ensuring high availability and reliability. The service benefits from the same fault-tolerant architecture that supports AWS's infrastructure globally, ensuring that applications remain accessible and performant even during regional outages. This guarantees that user management capabilities persist uninterrupted, aligning with strict availability SLAs.
Security
Corporate security standards are integral to Amazon Cognito, which employs sophisticated security measures to protect user information. All identity-related data is encrypted at rest and in transit, complying with industry regulations and best practices. Cognito's built-in Multi-Factor Authentication (MFA) and tracking of unusual sign-in activities enhance its security posture further. Developers can integrate it with AWS Identity and Access Management (IAM) to fine-tune user permissions and access control policies.
Competition
For developers considering alternatives to Amazon Cognito, several other cloud services offer comparable features. Google Cloud Identity Platform provides a Fully managed identity management service with robust OAuth 2.0 and OpenID Connect (OIDC) standards compliance. More information can be found here. Microsoft Azure Active Directory B2C allows for customizable user experiences, integrating with various identity providers, detailed here. Alibaba Cloud also offers IDaaS (Identity as a Service), which provides centralized identity management and access control for applications hosted on its cloud, detailed here.
In conclusion, Amazon Cognito stands as a robust identity management solution for developers and IT administrators who require a secure, scalable, and cost-effective user authentication and management service. With its broad set of features and interoperability with various AWS services, it helps streamline the app development process while enhancing security measures.
 Amazon GuardDuty
Amazon GuardDuty
 Amazon Athena
Amazon Athena
 AWS KMS
AWS KMS
 Amazon Macie
Amazon Macie